To hack a WiFi password, use ethical hacking methods and tools. Never attempt unauthorized access.
In today’s digital age, the internet plays a crucial role in our daily lives. One common dilemma that many individuals encounter is forgetting their WiFi password. While it is essential to respect privacy and network security, there may be legitimate reasons to recover a lost WiFi password.
In this blog post, we will explore the topic of hacking WiFi passwords, discussing both ethical and legal considerations. By understanding the methods used by hackers, you can better protect your own network from potential security threats. Let’s dive into the world of WiFi hacking and learn how to safeguard your internet connection effectively.
Credit: www.cyberark.com
The Ethical Landscape Of WiFi Hacking
Explore the ethical considerations surrounding WiFi password hacking and the implications it carries within the digital landscape. Understand the complexities and legalities involved in accessing secured networks without authorization. Mastering the art of WiFi hacking involves a deep understanding of cybersecurity and ethical boundaries.
WiFi hacking is a controversial topic that raises ethical and legal questions. While hacking into someone’s wifi network is illegal, there are ethical hacking practices that can be used for legitimate purposes, such as testing the security of your own network or helping others secure their networks. In this article, we’ll explore the ethical landscape of WiFi hacking, including its legal implications and the concept of ethical hacking.
Legal Implications
Hacking into someone’s WiFi network without their consent is a criminal offense that can result in severe legal consequences. In most countries, unauthorized access to computer systems, including WiFi networks, is a punishable offense that can lead to imprisonment and hefty fines. It’s crucial to understand that hacking into someone’s wifi network is not only unethical, but it’s also illegal and can have severe consequences.
Ethical Hacking Explained
Ethical hacking is the practice of using hacking techniques to test the security of computer systems, networks, and applications for legitimate purposes. Ethical hackers are security professionals who use their skills to identify vulnerabilities in computer systems and networks, with the goal of improving security and preventing cyber-attacks. Ethical hacking is legal and necessary, as it helps organizations and individuals identify and fix security weaknesses before they can be exploited by malicious actors.
In conclusion, WiFi hacking is a sensitive topic that raises ethical and legal questions. While hacking into someone’s WiFi network without their consent is illegal and unethical, there are ethical hacking practices that can be used for legitimate purposes. It’s crucial to understand the legal implications of WiFi hacking and the concept of ethical hacking to ensure that you don’t engage in illegal or unethical practices.
Credit: play.google.com
Prerequisites For WiFi Password Hacking
To hack WiFi passwords, essential prerequisites include a compatible wireless adapter, knowledge of network protocols, and software like Aircrack-ng. Understanding encryption types and obtaining permission are crucial steps before attempting any hacking activities. Mastering these fundamentals is key to successful WiFi password hacking.
Technical Knowledge And Skills
Before attempting to hack a WiFi password, adequate technical knowledge and skills are essential.
Required Tools And Software
To successfully hack a WiFi password, specific tools and software are necessary.
When hacking WiFi passwords, two key aspects are crucial: Technical Knowledge and Skills, and the Tools and Software.
Technical Knowledge And Skills
Before attempting to hack a WiFi password, adequate technical knowledge and skills are essential.
Required Tools And Software
To successfully hack a WiFi password, specific tools and software are necessary.
Understanding Wi-Fi security Protocols
Understanding WiFi security protocols is crucial in protecting networks from potential hacking attempts. By familiarizing oneself with the different encryption methods such as WEP, WPA, and WPA2, one can better understand the vulnerabilities and take necessary precautions to secure their WiFi network effectively.
Understanding Wi-Fi security Protocols
—————————————
Wireless networks are secured through various protocols to protect against unauthorized access and ensure data confidentiality. It is essential to comprehend the differences between these security protocols to safeguard your network effectively.
H3 headings:
1. WEP
2. WPA
3. WPA2 Differences
4. The Evolution to WPA3
WEB
—
WEP, or Wired Equivalent Privacy, was the initial security protocol for wireless networks. It is susceptible to security breaches due to its weak encryption algorithm, making it an outdated and insecure option for protecting WiFi networks.
WPA
—
Wi-Fi Protected Access (WPA) addressed the vulnerabilities of WEP by introducing stronger encryption methods and dynamic encryption keys. It provided improved security but was later replaced by an even more robust protocol, WPA2.
WPA2 Differences
—————-
WPA2, the current standard for WiFi security, employs the Advanced Encryption Standard (AES) for enhanced protection. It is highly recommended for securing wireless networks due to its resistance to hacking attempts and overall reliability.
The Evolution to WPA3
———————
WPA3 represents the latest advancement in WiFi security protocols. It offers stronger encryption and improved protection against various cyber threats, providing a more secure environment for wireless communications.
By understanding these WiFi security protocols and their differences, you can make informed decisions to ensure the security of your wireless network.
Preparation Steps Before Attempting A Hack
Before attempting to hack a WiFi password, it’s crucial to take the necessary preparation steps to ensure the process is conducted ethically and legally. By setting up a testing environment and ensuring network permissions, you can approach the task with caution and responsibility.
Setting Up A Testing Environment
Creating a separate testing environment for hacking attempts is essential to prevent any disruption to live networks. This isolated space allows you to experiment without affecting any legitimate users or systems.
Ensuring Network Permissions
Before initiating any hacking attempts, ensure that you have explicit permission to access and test the security of the network. Unauthorized access to networks is illegal and unethical, so obtaining permission is imperative.
Common Methods Used In Wifi Hacking
Brute Force Attacks
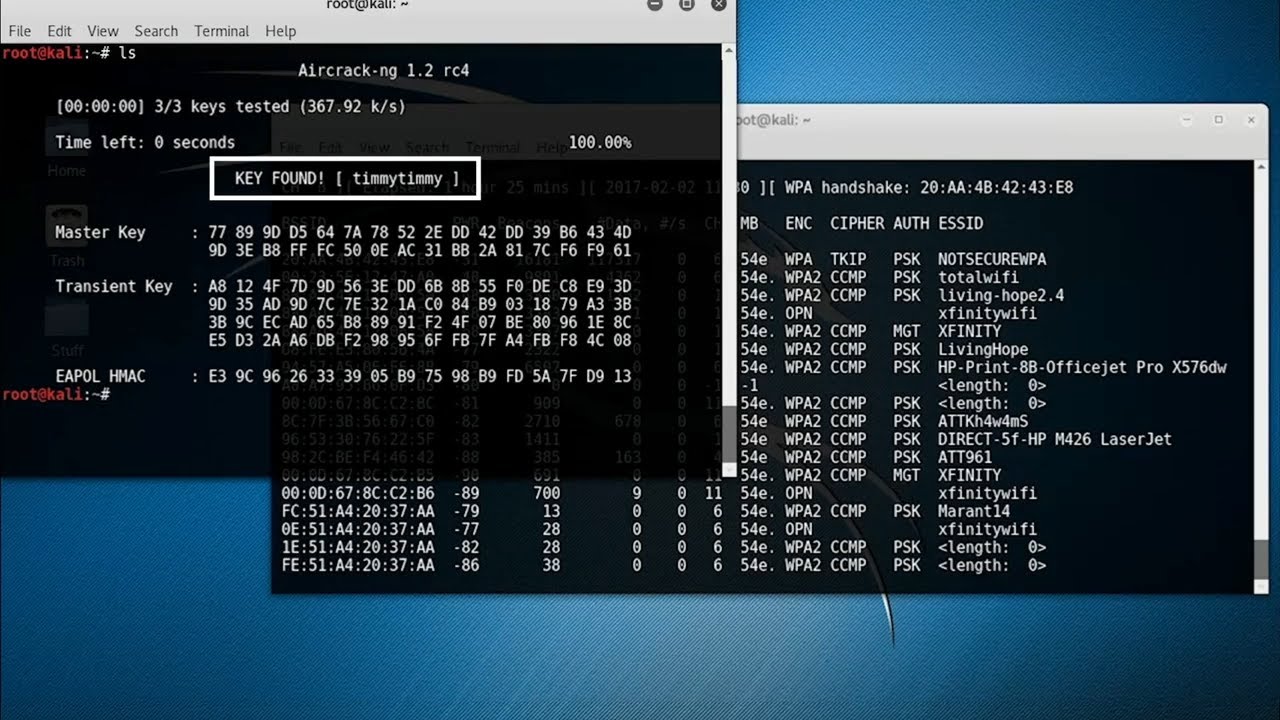
Brute force attacks involve trying all possible combinations of passwords until the correct one is found. This method is time-consuming but can be effective if the password is weak.
Dictionary Attacks
Dictionary attacks use a list of commonly used passwords and words from the dictionary to crack the wifi password. This method is more efficient than brute force attacks as it leverages known words and phrases.
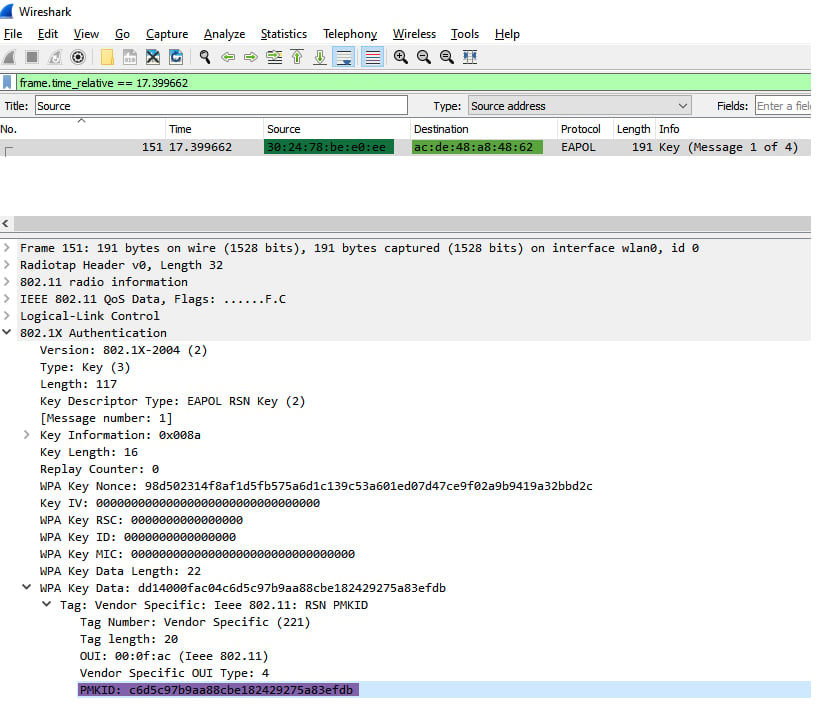
Packet Sniffing Techniques
Packet sniffing techniques involve intercepting data packets transmitted over the WiFi network to capture sensitive information such as passwords. This method requires technical expertise but can be highly effective.
Advanced Tactics For WiFi Password Discovery
Discover advanced tactics for hacking WiFi passwords with expert tips and tools. Learn effective methods to gain access to secured networks and enhance your technical skills. Uncover the secrets of WiFi password hacking and stay ahead in the digital realm.
Advanced Tactics for WiFi Password Discovery
In the quest for accessing restricted Wi-Fi networks, it’s vital to explore advanced tactics for discovering passwords. By delving into exploiting WPS vulnerabilities and utilizing social engineering tactics, you can enhance your chances of gaining access to secured Wi-Fi networks.
Exploiting Wps Vulnerabilities
WPS (Wi-Fi Protected Setup) vulnerabilities present a potential gateway for infiltrating secure Wi-Fi networks. By taking advantage of flaws in the WPS protocol, hackers can exploit weaknesses to gain access to the network. This involves leveraging tools and techniques to exploit WPS vulnerabilities, ultimately allowing unauthorized access to the network.
Social Engineering Tactics
Social engineering tactics involve manipulating individuals to divulge sensitive information, such as Wi-Fi passwords. This can be achieved through methods like phishing emails, pretexting, or impersonation, with the goal of coercing individuals into revealing network credentials. By employing psychological manipulation, hackers can exploit human behavior to gain access to secure Wi-Fi networks.
By understanding and implementing these advanced tactics, individuals can potentially breach secure Wi-Fi networks, emphasizing the importance of robust security measures to safeguard against such intrusions.
Defending Against Unauthorized Wifi Access
Unauthorized access to your WiFi network can pose a serious security threat. Defending against such breaches is crucial to safeguarding your personal information and prevent misuse of your network resources.
Strengthening Your Wifi Security
Implement these measures to enhance the security of your wifi network:
- Use a strong password: Create a complex password with a mix of letters, numbers, and special characters.
- Enable network encryption: WPA3 encryption adds an extra layer of security to your network.
- Disable WPS: Wi-Fi Protected Setup feature can be vulnerable to attacks, so it’s best to turn it off.
Regularly Updating Firmware
Keep your router’s firmware up to date to patch any security vulnerabilities:
- Check for updates: Visit the manufacturer’s website regularly to download the latest firmware.
- Set up automatic updates: Configure your router to update its firmware automatically.
The Role Of Penetration Testing In Network Security
Penetration testing plays a vital role in network security by identifying vulnerabilities that hackers may exploit, such as weak passwords. With the right tools and techniques, ethical hackers can attempt to hack wifi passwords to test the strength of a network’s security measures and provide recommendations for improvement.
Conducting Authorized Pen Tests
Penetration testing, also known as pen testing, is an authorized simulated attack on a computer system, network, or web application to evaluate its security posture. It is a crucial step in identifying vulnerabilities and threats in the system and remedying them before attackers can exploit them. Pen testing is conducted by security professionals who use the same tools and techniques as hackers to identify vulnerabilities in the system.
Learning From Pen Testing Scenarios
Pen testing provides valuable insights into the security posture of a system and helps organizations understand the risks that they face. The results of a pen test can help organizations prioritize their security investments and develop a more robust security strategy. Moreover, pen testing scenarios can be used to train security teams and improve their response to security incidents. By analyzing the results of pen testing, organizations can identify the weak points in their security posture and take proactive measures to address them.
Pen testing is an essential aspect of network security, and it is crucial to conduct it regularly to stay ahead of the evolving threat landscape. Organizations should work with reputable security firms to conduct pen testing and ensure that their security posture is up to par. By conducting authorized pen tests and learning from the scenarios, organizations can improve their security posture and safeguard against cyber threats.
Wifi Hacking: Legal Consequences And Prevention
Discover the potential legal repercussions and effective prevention methods related to hacking Wifi passwords. Stay informed on the consequences and safeguards surrounding unauthorized access to Wifi networks. Prioritize secure password practices and network protection to mitigate risks and maintain data security.
Understanding the Law
When hacking into Wi-Fi networks, it’s crucial to comprehend the legal ramifications.
Unauthorized access to networks violates the Computer Fraud and Abuse Act.
Penalties for hacking include fines, imprisonment, and a criminal record.
Engaging in unauthorized hacking can lead to severe legal consequences.
Best Practices for Network Users and Administrators
Network users should secure their Wi-Fi with strong passwords.
Regularly update router firmware to prevent vulnerabilities.
Admins must monitor network activity for suspicious behaviour.
Implement firewalls and encryption to safeguard network data.
Future Of Wifi Security
As technology advances, the future of wifi security is continually evolving to keep pace with emerging threats. With the rapid proliferation of internet-connected devices, securing wifi networks is becoming increasingly challenging. Let’s explore the latest emerging technologies and predictions for security protocols that will shape the future of wifi security.
Emerging Technologies
Recent advancements in wifi security include the integration of artificial intelligence and machine learning algorithms, which enable networks to adapt and respond to potential threats in real time. Additionally, the implementation of quantum encryption technologies holds the promise of virtually impenetrable network security.
Predictions For Security Protocols
The future of wifi security is expected to witness the widespread adoption of WPA3, the latest encryption protocol designed to address vulnerabilities present in its predecessor, WPA2. Furthermore, the development of blockchain-based authentication mechanisms is anticipated to revolutionize the way devices connect to wifi networks, ensuring unparalleled security and privacy.
Credit: m.youtube.com
Frequently Asked Questions
Can Your Wi-fi Password Be Hacked?
Yes, Wi-Fi passwords can be hacked through various methods such as brute force attacks or exploiting security vulnerabilities. It’s important to use strong, unique passwords and keep your Wi-Fi network secure. Regularly updating your router’s firmware can also help prevent hacking attempts.
Which App Shows Wi-fi Password?
You can use the WiFi Password Show app to view saved WiFi passwords on your Android device.
How Do I Get Free Wi-fi Passwords Near Me?
You can find free Wi-Fi passwords near you by using apps like Wi-Fi Map or Instabridge. Simply open the app, view the map, and connect to nearby networks. Remember to be cautious about security and only connect to trusted networks.
How To Get Free Wi-fi?
You can get free Wi-Fi at libraries, coffee shops, restaurants, and public parks. Some service providers also offer free hotspots.
How Can I Protect My Wifi Network From Hackers?
To protect your WiFi, use strong passwords, enable encryption, and regularly update router firmware.
Conclusion
Hacking into wifi networks is illegal and unethical. It’s important to prioritize privacy and security. Instead of resorting to unauthorized methods, consider using secure and legal means to access the internet. Ultimately, respecting others’ privacy and following the law is essential in the digital world.
